Tag: the basics
-

As a Security Engineer, what you need to know about ephemeral ports
What are ephemeral ports? Ports are used for sending and receiving data between devices, same like how ships use ports to send and receive goods. Now ephemeral ports are temporary ports that are used to send/recieve data. For commonly used services ports have port numbers associated for them for example SSH is port number 22,…
-

Top 10 Security tools every security engineer must know
I always emphasize tools are not everything but we need to know how they work, how tools are engineered and how they make our lives easier. Once you have the engineering understanding of how the tool is working you can take full potential of the same.
-

What is MDR?
MDR stands for Managed Detection Response. Its a type of Detection Response and before we dive deep into MDR let’s understand what is Detection Response and will discuss about MDR later in the post. Topics we will be covering this post
-

-

Xtreme Breakdown – Secure Hashing
What is the purpose of Hashing or what is the problem that it’s trying to solve? Let’s say you are trying to send a file from your device to your friend’s device and your friend would like to confirm whether the file you sent is the same file that is downloaded the same file or…
-

Brief Encyclopedia of CVSS
We have seen that there is a lot of noise going around CVSS as FIRST has launched version 4.0 and in this article, I would like to discuss what is CVSS and how it evolved. What is CVSS CVSS stands for Common Vulnerability Scoring System. NIAC unveiled it on 23 February 2005. The purpose of…
-

CVSS Infographic
CVSS is the scoring system managed and launched by the Forum of Incident Response and Security Teams(FIRST) but started by the National Information Assurance Partnership (NIAP) Here is the infographic that explains the journey of CVSS from birth to what it is today. I am going to write a detailed guide on how versions changed…
-

CVE vs CWE – The Layman Guide
When it comes to information security there are many standards, guides, frameworks and terminologies that you must learn to understand Infosec better. In this guide, I will help you understand the difference between two Acronyms that we use every day and also help you to understand when to use what. What is CVE? CVE stands…
-
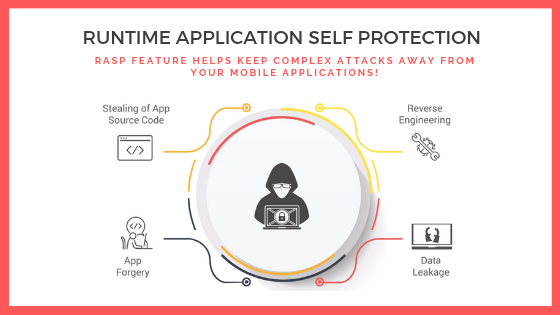
What is Runtime Application Self Protection(RASP)
What is RASP? RASP stands for Runtime Application Self Protection, it is a technology that secures applications in runtime. RASP starts whenever any application configured with RASP executes and it protects the application in real-time. RASP intercepts all the calls between the app and the system validates them and makes sure they are secure. Whenever…
-

Free Malware scanners for WordPress
Ask anyone who has a website, the worst thing that could happen to his/her website is malware. What is malware? Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network. Once any device is infected with malware the controller will have full control of the infected device. Again…
