-
Memory Segmentation In a Nutshell
Memory segmentation is a place where all the things happen while any program is running. Memory is divided into several segments and in this article, we are going…
4 min read
-
Securing Cookies. Beyond document.cookie
Cookies is the place where the web applications store the authentication data. If you can able to impersonate target cookie in your browser then you can directly login…
4 min read
-
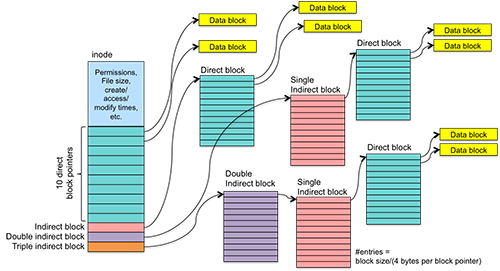
What is UFS – Unix File System and ext Family
Knowing about Unix File System is important because it is the file system that is used by Linux distros and it is one of the most used kernels…
4 min read
-
NTFS File System Basics and Structure
Even though FAT is one of the widely used file system it lacks many features. When Windows is about to launch Windows NT, which is sever based operating…
4 min read
-
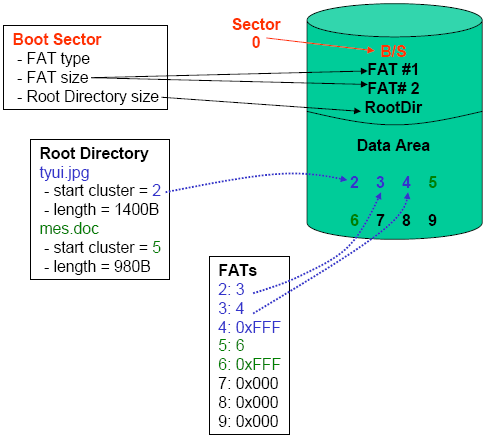
Everything a Security Analyst need to know about FAT File System
For understanding disk-based forensics we need to know about each file system, how it works and what it’s made up of. In this article we will share…
4 min read
-
Everything you need to know about File System Basics as a Forensic Analyst
What operating system do you use? Linux, Windows or Mac? Whatever the operating system you are using it doesn’t matter. You will be storing files in it. Every…
4 min read