Author: Manindra Simhadri
-
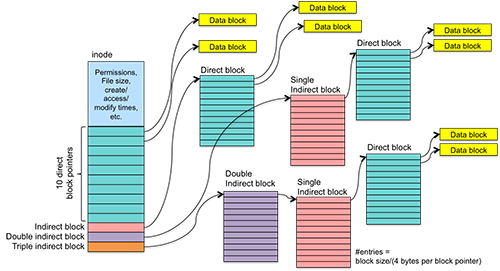
What is UFS – Unix File System and ext Family
Knowing about Unix File System is important because it is the file system that is used by Linux distros and it is one of the most used kernels out there. XFS, JFS and many more file systems are like UFS so if you know about this file system you can cover other file systems based…
-

NTFS File System Basics and Structure
Even though FAT is one of the widely used file system it lacks many features. When Windows is about to launch Windows NT, which is sever based operating system they want to launch a new file system that can have capabilities that FAT doesn’t have.
-
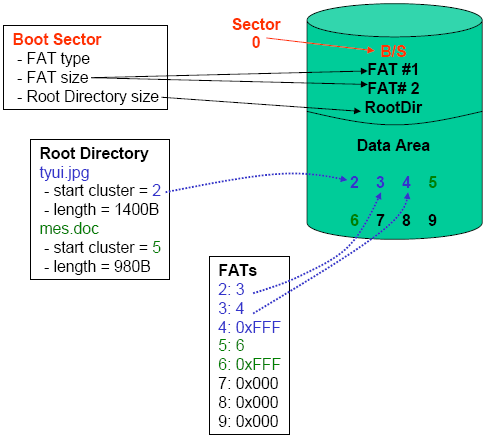
Everything a Security Analyst need to know about FAT File System
For understanding disk-based forensics we need to know about each file system, how it works and what it’s made up of. In this article we will share you everything that we know, and you should know about FAT FAT stands for File Allocation Table. It is one of the most widely used file system…
-

Everything you need to know about File System Basics as a Forensic Analyst
What operating system do you use? Linux, Windows or Mac? Whatever the operating system you are using it doesn’t matter. You will be storing files in it. Every operating system uses their kind of file system. Windows uses NTFS, Linux uses FAT and there are different types of FAT systems too. So, to create any…
-

Secure way to access dark web on android
Everything is on mobile and when we analyze the traffic we are getting to internet most of the sources are from mobile. Every web application is making their mobile apps. But for most of the people who wants to access dark web their first choice is desktop or laptop. To make it handy I have…
-

What is DNS Poisoning? Kali Linux tutorial to find Facebook Password
DNS poisoning is one of the way to attack the users present in same network. In this article I am going to share what is DNS poisoning, how we can do it and what are the details we can get using this attack. What is DNS? DNS stands for Domain Name Server. This is a…
-

How OWASP Top 10 Will Protect Web Application
When you look in the requirements of any information security analyst OWASP top ten will be there for sure. Firm knowledge on OWASP top 10 OWASP stands for Open Web Application Security Project. This is a non-profit organization with the mission to make web securely visible. Web is made to be available not secure so…
-

How to access Dark Web or Deep Web for noobs
You might be hearing these two words dark web and deep web quite for a while. Both are almost same but not same, just almost. You cannot access dark web from a normal browser you are using like from google chrome or Firefox. Here in this tutorial I am going to share you how to…
-

What is Supply Chain Attack: The Attack That Keeps Every WordPress Site Vulnerable
There are many attacks that are happening on the internet. Each attack belongs to some type of attack family. One of my friend works in PayPal and he said PayPal alone gets 3000 attacks per second and imagine how many attacks are carried out worldwide. In this article I am going to explain to you…
-

How to find IP address of anyone
To attack anyone the first thing you must know is to find the IP address of the target. There are many tools that help to find IP address but here in this tutorial I will help you with the tool called IP puller or IP logger. IP logger grabs the IP address of the victim…
